Drivers around Europe have been warned not to scan QR codes for parking tickets due to a recent incident where threat actors tricked unsuspecting victims into scanning malicious QR codes and entering personal information. In this article, we’ll discuss how QR code scams work, the risks they pose, and how you can protect your business with Hornetsecurity’s Advanced Threat Protection and its unique QR Code Analyzer. With the increasing reliance on QR codes for everyday transactions, understanding these threats has never been more critical.
A Quick Response way to get compromised
Let’s start with the basics. QR (Quick Response) codes were invented in Japan over 25 years ago to track car parts in the supply chain. Today QR codes are everywhere in our everyday life: want to see the restaurant menu on your phone? Just scan the QR code. Need to pay for your car parking? Scan the QR code. Must sign into the venue for Covid-19 tracking? Scan the QR code. Need to pay a delivery fee for your parcel? Just scan the QR code in this email.
Hopefully, you see the pattern here; we’re training people to scan QR codes as a “normal activity” with the expectation of something good or useful happening as a result. Plus, unlike an actual website address at the bottom of a business card or a movie poster, we have no way to tell if the QR code leads to a legitimate site or experience.
Understanding Quishing as a New Frontier in Cyber Threats
Cybercriminals have quickly seized this opportunity, with QR code phishing (commonly referred to as “quishing”) emerging as a prominent threat. This is not just limited to online attacks but is increasingly becoming a global issue. In recent months, we’ve seen a new trend in parking-related scams across Europe, where fake QR codes have been stuck on parking meters to steal users’ financial information. The QR codes lead to fraudulent websites where the driver is asked to share payment details with scammers.
The UK’s RAC has reacted to these attacks saying: “As if this quishing scam isn’t nasty enough, it can also lead to drivers being caught out twice if they don’t realise they haven’t paid for parking and end up getting a hefty fine from the council”.
Unlike traditional phishing, where malicious links are visible in emails, QR code phishing disguises these harmful URLs in the form of an innocent-looking QR code which leads to phishing sites or initiates malware downloads.
Deciphering URLs in any case is very hard to do, and even experienced security professionals can’t easily tell if an address is safe or dangerous. But at least with a written-out web address, you have some chance of judging how trustworthy it looks – with a QR code you’re completely in the dark.
The Rising Threat of Quishing in Corporate Settings and Why Businesses Are Targeted
It’s important to note that the risk of quishing isn’t limited to individual consumers. Businesses are increasingly becoming the primary targets of these attacks. Many organizations now use QR codes for various purposes, such as event registrations and remote work access, leading employees to interact with QR codes daily.
This heightened usage in corporate environments makes them particularly susceptible to cybercriminals who send targeted quishing emails to employees. It is concerning that many employees may be unaware of the potential risks of scanning unknown codes and may unknowingly grant access to company data.
In some instances, quishing emails are designed to look like internal communications, tricking employees into thinking the code is safe because it seems to come from a trusted source.
Quishing attacks are also used by cybercriminals to spread malware, sending users to websites that automatically download harmful software once scanned. These attacks can be devastating for businesses, leading to extended downtime, data loss, and hefty regulatory fines if sensitive customer information is exposed.
For QR codes you scan with your phone – make sure to use the preview feature which shows you the URL that the QR code is pointing to before actually opening it in the browser.
Generating a QR code (and thus QR code scams) is easy; use any of the many free generators online. All you need to do is enter the URL you want to be embedded in the image, download the resulting QR code, and put it on your restaurant menu or in your email footer.
For example, this QR code leads to Hornetsecurity’s home page, but there’s no way to tell that by looking at it:
There’s no such thing as a malicious QR code itself; it’s the target of the link that might be a promotion for a new product, with the opportunity to win a new laptop or a phishing site that’ll steal your information for criminal purposes. So, whenever someone talks about legitimate QR codes or a fake QR code, they’re referring to the target URL of the QR code image.
The links in QR code scams can also lead to a file download(PDF, Word document, etc.) or an application that can contain malware that will infect your device. Once the infection takes place, the malware can continue to spread and conduct its illicit activities.
Other behavior that is seen is that scanning a QR code can create a new email in your mail program and send it *on your behalf*! Since it will be from you, it will increase the likelihood that the recipients will trust the content – which could be another malicious QR code. Surprise!
QR Code scams
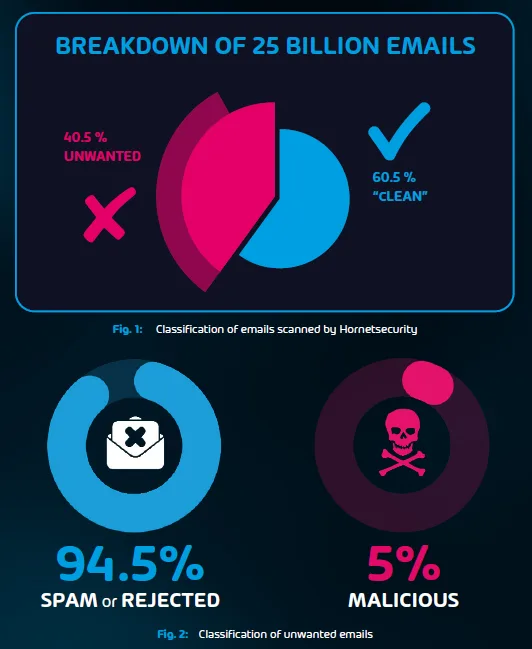
The main attack vector in a business setting for targeted malicious QR code scams is via email. Other avenues to get the QR code in front of your users include printed snail mail marketing and of course, printing QR codes out as QR code stickers and sticking them over existing ones in restaurants, etc. around your office buildings.
This approach requires physical proximity and will also give a jarring experience for end users – if they’re expecting a cafe menu when they scan the QR code but get a site where they have to login, they’re much more likely to sense that something is off.
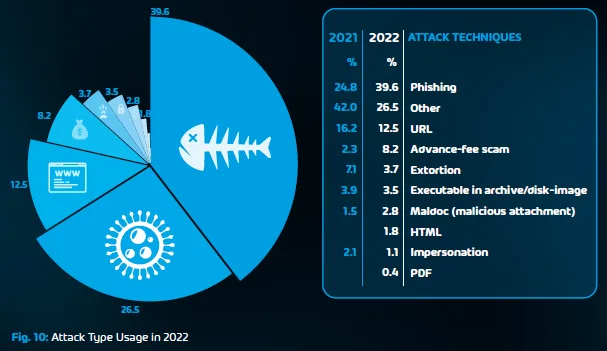
Also from our Cyber Security Report, here’s the breakdown of different email attack techniques in 2022 and 2023.
The reason email-borne QR code scams are on the rise is because most email filtering systems are very good at catching standard malicious links. The way this attack typically works is an attacker compromises a legitimate website and uses it to send out emails with normal text links to the site embedded along with some enticing reason for the user to click the link.In many cases, malicious payloads are hosted there for the users to unknowingly download malware.
Alternatively,the site shows a “real looking” login page to harvest the user’s username, password, and potentially other sensitive information.
That all said, most email hygiene solutions cannot scan a QR code or images of any kind and thus are completely oblivious to the danger lurking in those little black and white QR code squares, increasing the risk that the attacker slips their malicious link through your defenses.
A common, generic (meaning it’s not customized to your organization, but simply sprayed out to millions of email inboxes) type of QR code phishing email attack is “failed delivery by FedEx” or a similar shipping company. Scanning the QR code will allow you to pay a fee to release the (non-existent) parcel.
Another variant is the failed payment lure, where you scan the QR code and then have to enter some details on a page to finalize a payment.
As you can appreciate, the hit rate on these types of attacks will be very low, but if you can send them out in sufficient numbers, even a small number of people falling for these QR codes can bring in serious amounts of money.
The Alarming Rise of Targeted QR Code Attacks
What’s more concerning, however, is targeted QR code attacks (a form of spear-phishing) where phishing emails are customized to your organization and users, which if done well, can substantially increase the risk of compromise. The lures in these phishing emails will be especially compelling for your users, possibly matching other emails they are expecting, with content that is “normal” for them to deal with, perhaps containing financial information.
This could be because they’ve compromised an email system at another organization and have investigated what normal email traffic looks like and then spring QR code phishing scams, with an even higher likelihood of trust, as the email with the fraudulent QR code will be coming from a trusted business partner.
Stop malicious QR codes in their tracks
The new QR Code Analyzer is a unique feature of Hornetsecurity’s Advanced Threat Protection and is built in to help you avoid QR code scams. There aren’t even configuration options for it in the Control Panel, it just scans every single QR code in each email, follows the link, and verifies if it’s malicious or not. Simple!
Just like with any other malicious content in an email, emails with QR code scams will be blocked before they reach end-user mailboxes.
Hornetsecurity’s QR Code Analyzer not only scans QR codes in real-time but also follows the embedded links to ensure they are legitimate before allowing them to reach users’ inboxes. This proactive approach ensures that even the most sophisticated quishing attacks are caught before they can do any harm.
And that’s the mark of good security products; they do their work unseen in the background, keeping your users safe and protected, in this case from a QR code scam.
Cybersecurity Best Practices for QR Code Safety
Outside of business email, to complete the protection of your users from fake QR codes, include the following regarding QR codes in your regular cyber security awareness training:
- Don’t ever pay invoices or fees via a QR code, wherever it’s displayed. Connect to the organization’s website in your browser instead and look up any required payment there;
- Don’t use a QR code analyzer app for scanning QR codes on your phone; both the Android and iOS’s camera apps have this functionality built in;
- Always use the URL preview after the QR code is scanned to see the link that the QR code sends before opening it in your browser;
- If any link (from a QR code or otherwise) looks suspicious, pick up the phone and call to double-check before proceeding. Better safe than sorry. This is particularly important if the email or linked website’s URL deals with financial information.
Protect your business from the growing threat of QR code scams with Hornetsecurity’s Advanced Threat Protection. Our unique QR Code Analyzer automatically scans and blocks malicious QR codes before they reach your inbox. Stay one step ahead of cybercriminals and ensure your team’s safety.
CONCLUSION
As QR code scams continue to evolve, awareness and vigilance are your best defenses. Understanding the risks associated with quishing and implementing best practices can help safeguard both your personal and business information. By educating your users and utilizing tools like Hornetsecurity’s QR Code Analyzer, you can significantly reduce the threat posed by these insidious scams. Stay proactive, keep security at the forefront, and ensure that your organization remains a step ahead of cybercriminals. Protecting your digital environment starts with informed actions—don’t let QR codes become a gateway to compromise.
