Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on industry items from the month of September, while discussing hard data points from our own services for Q3 of 2024.
As a reminder, some months ago we shifted from discussing the data points mentioned here on a monthly basis, to instead discussing them quarterly. We felt that this would more easily show the shifts in attack trends as opposed to the micro changes we had been seeing on a monthly basis outside of major incidents (which often warrant their own article).
Executive Summary
- There was a higher percentage of threats delivered by email in Q3 when compared with Q2.
- The amount of low-effort (and ultimately rejected) email attacks increased during the months of July, August, and Sept by a small amount.
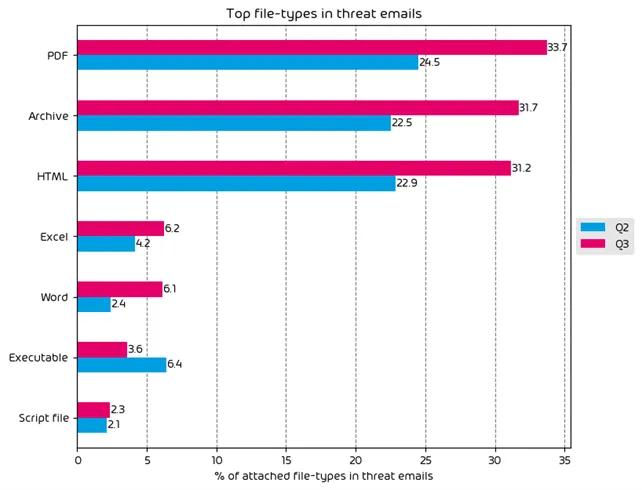
- PDFs, archive files, and HTML files were the most popular malicious email file types during the data period for this report.
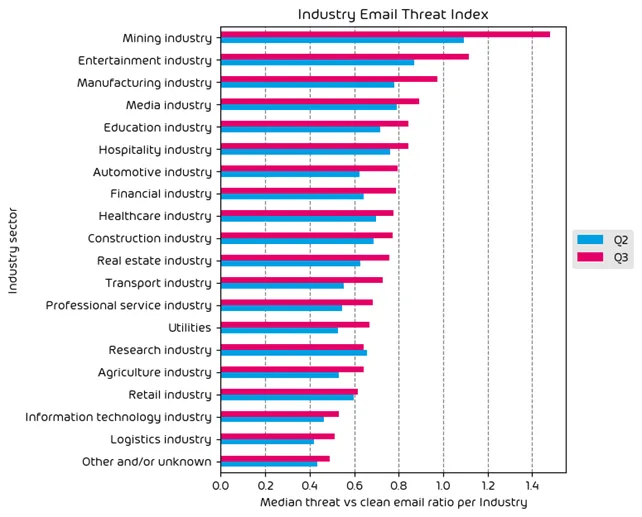
- Mining, entertainment, and Manufacturing are the most targeted verticals during the data period.
- There was a noted increase in the threat index for nearly every single industry vertical during Q3.
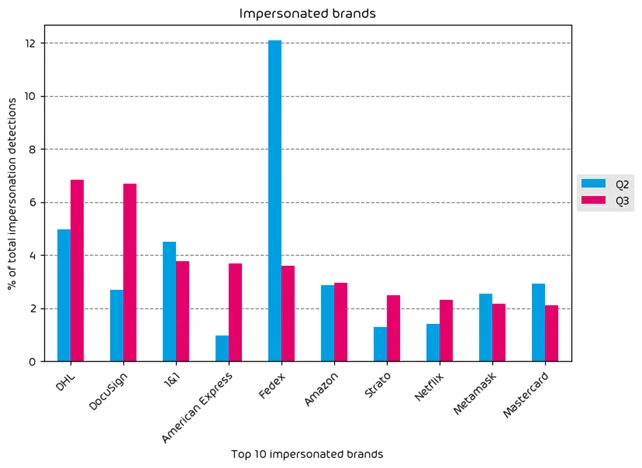
- DHL and DocuSign were the 2 most impersonated brands during Q3.
- We observed a marked increase in American Express brand impersonations during Q3, likely driven by the summer travel season.
- Microsoft recently held a Windows Security Summit to discuss the fallout from the CrowdStrike incident and are now beginning to discuss some long term plans to prevent the issue from happening again.
- A high severity CUPS vulnerability allow remote code execution has admins double-checking their Linux systems
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for Q2 (Apr-Jun) 2024 compared to Q3 (Jul-Sep) 2024.
Our data shows that more email threats were levied at businesses during Q3 than Q2. This is a fairly consistent trend from year to year as it’s common to see the amount of threats decrease during summer months. Threat actors know that fewer people are in the office during this time frame and as such less traffic during Q2 is normal. This trend frequently blends into Q3 somewhat as well as July and August are also heavy travel months. We suspect the amount of threatening email to increase now throughout the remainder of the year.
Worth noting for Q3 specifically, we saw an increase in the amount of rejected email threats. These are threats tend to be low-effort email attacks that cast a wide net instead their spear phishing counterparts. Regardless, the email security threat level remains high overall.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
Industry Email Threat Index
Impersonated Company Brands and Organizations
Major Incidents and Industry Events
Microsoft Making Changes Due to CrowdStrike
New NIST Guidelines for Passwords
CUPS Remote Code Execution Vulnerability
One other big security news item making headlines over the last month is the news or a new severe vulnerability in the Linux CUPS printing system. CUPS stands for Common UNIX Printing System, and is generally not in a running state on most Linux systems. That said, if the service is running it will listen on UDP port 631 and will allow connections from any device on the network for the purposes of creating a new printer.
This state could potentially allow a remote code execution via a number of different tracked CVEs listed below:
Effective mitigations includes disabling the running service, or blocking and/or tightly controlling access to UDP port 631.
Predictions for the Coming Months
- Email threats are likely to continue the upward trend for the remainder of the year due to the coming Christmas holiday shopping season
- due to the nature of threat finding, it’s possible we’ll see additionally discovered vulnerabilities in popular and common open source systems and libraries.
Monthly Recommendations
- Prepare your end users for the upcoming increases in email threats by leveraging a trusted security awareness training vendor to get them up to speed.
- If you’ve got any Linux systems in-house, make sure to check them for risks associated with the current CUPS vulnerabilities. Mainly check access to UDP port 631.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 75,000 customers.
